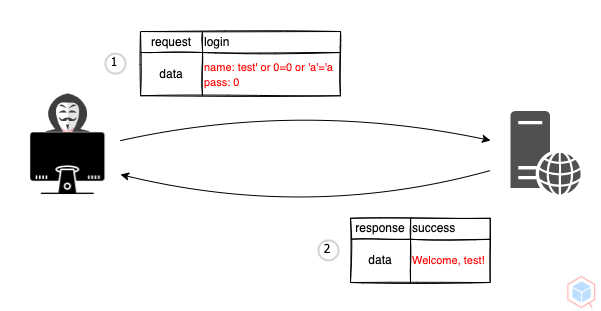
A threat actor may alter the XML path language (XPath) query to read data on the target (This is more dangerous than SQL injection because it may allow querying the whole database - XML document)
(XPath is a language that queries XML documents - the XPath expression is a locator)
- Threat actor submits a malicious XPATH query to a vulnerable target
- The target parses the malicious query (that contains expressions called a locator) and returns data from the database (XML document)
<users>
<user>
<name>test</name>
<pass>P@ssw0rd!01</pass>
</user>
</users>...
String xpath_query = "//user[name/text()='" + get("name") + "' And pass/text()='" + get("pass") + "']";
...name: test' or 0=0 or 'a'='a
pass: 0
//String xpath_query = "//user[(name/text()='test' or 0=0) or ('a'='a' And pass/text()='P@ssw0rd!01')]";
Welcome, test!
High
- XPATH Injection
- Read data
- Input validation
- Parametrized queries
6c020d48-9b20-4011-a513-36676994ee8e