diff --git a/README.md b/README.md
index 1e7d49ec7..91a9a59b4 100644
--- a/README.md
+++ b/README.md
@@ -18,7 +18,7 @@ The Operator to install and manage the lifecycle of the [Kuadrant](https://githu
* [If you are an API Provider](#if-you-are-an-api-provider)
* [If you are a Cluster Operator](#if-you-are-a-cluster-operator)
* [User guides](#user-guides)
-* [Kuadrant Rate Limiting](#kuadrant-rate-limiting)
+* [Kuadrant Rate Limiting](#kuadrant-rate-limiting)
* [Documentation](#documentation)
* [Contributing](#contributing)
* [Licensing](#licensing)
@@ -32,29 +32,30 @@ more reusable and leverage the underlying kubernetes platform. It aims to delive
of applications & services when it comes to rate limiting, authentication, authorization, discoverability, change management, usage contracts, insights, etc.
Kuadrant aims to produce a set of loosely coupled functionalities built directly on top of Kubernetes.
-Furthermore it only strives to provide what Kubernetes doesn’t offer out of the box, i.e. Kuadrant won’t be designing a new Gateway/proxy,
+Furthermore, it only strives to provide what Kubernetes doesn’t offer out of the box, i.e. Kuadrant won’t be designing a new Gateway/proxy,
instead it will opt to connect with what’s there and what’s being developed (think Envoy, Istio, GatewayAPI).
Kuadrant is a system of cloud-native k8s components that grows as users’ needs grow.
+
* From simple protection of a Service (via **AuthN**) that is used by teammates working on the same cluster, or “sibling” services, up to **AuthZ** of users using OIDC plus custom policies.
* From no rate-limiting to rate-limiting for global service protection on to rate-limiting by users/plans
## Architecture
Kuadrant relies on [Istio](https://istio.io/) and the [Gateway API](https://gateway-api.sigs.k8s.io/)
-to operate the cluster (istio's) ingress gateway to provide API management with **authentication** (authN),
+to operate the cluster (Istio's) ingress gateway to provide API management with **authentication** (authN),
**authorization** (authZ) and **rate limiting** capabilities.
### Kuadrant components
-| CRD | Description |
-| --- |---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
-| Control Plane | The control plane takes the customer desired configuration (declaratively as kubernetes custom resources) as input and ensures all components are configured to obey customer's desired behavior.
This repository contains the source code of the kuadrant control plane |
-| [Kuadrant Operator](https://github.com/Kuadrant/kuadrant-operator) | A Kubernetes Operator to manage the lifecycle of the kuadrant deployment |
-| [Authorino](https://github.com/Kuadrant/authorino) | The AuthN/AuthZ enforcer. As the [external istio authorizer](https://istio.io/latest/docs/tasks/security/authorization/authz-custom/) ([envoy external authorization](https://www.envoyproxy.io/docs/envoy/latest/configuration/http/http_filters/ext_authz_filter) serving gRPC service) |
-| [Limitador](https://github.com/Kuadrant/limitador) | The external rate limiting service. It exposes a gRPC service implementing the [Envoy Rate Limit protocol (v3)](https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/ratelimit/v3/rls.proto) |
-| [Authorino Operator](https://github.com/Kuadrant/authorino-operator) | A Kubernetes Operator to manage Authorino instances |
-| [Limitador Operator](https://github.com/Kuadrant/limitador-operator) | A Kubernetes Operator to manage Limitador instances |
+| CRD | Description |
+|----------------------------------------------------------------------|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
+| Control Plane | The control plane takes the customer desired configuration (declaratively as kubernetes custom resources) as input and ensures all components are configured to obey customer's desired behavior.
This repository contains the source code of the kuadrant control plane |
+| [Kuadrant Operator](https://github.com/Kuadrant/kuadrant-operator) | A Kubernetes Operator to manage the lifecycle of the kuadrant deployment |
+| [Authorino](https://github.com/Kuadrant/authorino) | The AuthN/AuthZ enforcer. As the [external istio authorizer](https://istio.io/latest/docs/tasks/security/authorization/authz-custom/) ([envoy external authorization](https://www.envoyproxy.io/docs/envoy/latest/configuration/http/http_filters/ext_authz_filter) serving gRPC service) |
+| [Limitador](https://github.com/Kuadrant/limitador) | The external rate limiting service. It exposes a gRPC service implementing the [Envoy Rate Limit protocol (v3)](https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/ratelimit/v3/rls.proto) |
+| [Authorino Operator](https://github.com/Kuadrant/authorino-operator) | A Kubernetes Operator to manage Authorino instances |
+| [Limitador Operator](https://github.com/Kuadrant/limitador-operator) | A Kubernetes Operator to manage Limitador instances |
### Provided APIs
@@ -86,7 +87,7 @@ Additionally, Kuadrant provides the following CRDs
### Installing Kuadrant
-Installing Kuadrant is a two-step procedure. Firstly, install the Kuadrant Operator and seconly,
+Installing Kuadrant is a two-step procedure. Firstly, install the Kuadrant Operator and secondly,
request a Kuadrant instance by creating a *Kuadrant* custom resource.
#### 1. Install the Kuadrant Operator
@@ -98,14 +99,14 @@ The Kuadrant Operator is available in public community operator catalogs, such a
The operator is available from [OperatorHub.io](https://operatorhub.io/operator/kuadrant-operator).
Just go to the linked page and follow installation steps (or just run these two commands):
-```
+```sh
# Install Operator Lifecycle Manager (OLM), a tool to help manage the operators running on your cluster.
-$ curl -sL https://github.com/operator-framework/operator-lifecycle-manager/releases/download/v0.23.1/install.sh | bash -s v0.23.1
+curl -sL https://github.com/operator-framework/operator-lifecycle-manager/releases/download/v0.23.1/install.sh | bash -s v0.23.1
# Install the operator by running the following command:
-$ kubectl create -f https://operatorhub.io/install/kuadrant-operator.yaml
+kubectl create -f https://operatorhub.io/install/kuadrant-operator.yaml
```
**Openshift**
@@ -125,12 +126,13 @@ kubectl create namespace kuadrant
Apply the `Kuadrant` custom resource:
-```yaml
-kubectl apply -n kuadrant -f -<\t\t\t\t{extra-values-as-json}`
diff --git a/doc/proposals/authpolicy-crd.md b/doc/proposals/authpolicy-crd.md
index 78f2fa56c..f53bd7aeb 100644
--- a/doc/proposals/authpolicy-crd.md
+++ b/doc/proposals/authpolicy-crd.md
@@ -9,14 +9,14 @@ The new [GatewayAPI](https://gateway-api.sigs.k8s.io/) defines a standard [polic
## Goals
With `targetRef` from policy attachment concept, following are the goals:
-- Application developer should be able target [`HTTPRoute`](https://gateway-api.sigs.k8s.io/v1alpha2/references/spec/#gateway.networking.k8s.io/v1alpha2.HTTPRoute) object in their own namespace. This will define authorization policy at the hostname/domain/vHost level.
+- Application developer should be able to target [`HTTPRoute`](https://gateway-api.sigs.k8s.io/v1alpha2/references/spec/#gateway.networking.k8s.io/v1alpha2.HTTPRoute) object in their own namespace. This will define authorization policy at the hostname/domain/vHost level.
- Cluster operator should be able to target [`Gateway`](https://gateway-api.sigs.k8s.io/v1alpha2/references/spec/#gateway.networking.k8s.io/v1alpha2.Gateway) object along with HTTPRoute in the gateway's namespace. This will define policy at the listener level.
- To reduce context sharing at the gateway and external authorization provider, action type and auth-provider are defaulted to `CUSTOM` and authorino respectively.
## Proposed Solution
Following is the proposed new CRD that combines policy attachment concepts with Istio's AuthorizationPolicy:
-```yaml=
+```yaml
apiVersion: kuadrant.io/v1beta1
kind: AuthPolicy
metadata:
@@ -50,7 +50,7 @@ status:
reason: HTTPRouteProtected/GatewayProtected/Error
status: "True" | "False"
type: Available
- observedGeneration: 1
+ observedGeneration: 1
```
### Target Reference
@@ -84,7 +84,7 @@ status:
- `methods`: a method matches over request method like `DELETE`.
Fields in a rule object are ANDed together but inner fields follow OR semantics. For example,
-```
+```yaml
hosts: ["*.toystore.com"]
methods: ["GET", "POST"]
paths: ["/admin"]
@@ -100,7 +100,7 @@ AuthScheme is embedded form of [Authorino's AuthConfig](https://github.com/Kuadr
The example AuthPolicy showed above will create the following AuthConfig:
-```yaml=
+```yaml
apiVersion: authorino.kuadrant.io/v1beta1
kind: AuthConfig
metadata:
diff --git a/doc/proposals/rlp-target-gateway-resource.md b/doc/proposals/rlp-target-gateway-resource.md
index 1463adcba..57771dce5 100644
--- a/doc/proposals/rlp-target-gateway-resource.md
+++ b/doc/proposals/rlp-target-gateway-resource.md
@@ -12,7 +12,7 @@ Having in place this HTTPRoute - Gateway hierarchy, we are also considering to a

-On designing kuadrant rate limiting and considering Istio/Envoy's rate limiting offering, we hit two limitations ([described here](https://docs.google.com/document/d/1ve_8ZBq8TK_wnAZHg69M6-f_q1w-mX4vuP1BC1EuEO8/edit#bookmark=id.5wyq2fj56u94)). Therefore, not giving up entirely in existing [Envoy's RateLimit Filter](https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/filters/network/ratelimit/v3/rate_limit.proto#extension-envoy-filters-network-ratelimit), we decided to move on and leverage the Envoy's [Wasm Network Filter](https://www.envoyproxy.io/docs/envoy/latest/configuration/listeners/network_filters/wasm_filter) and implement rate limiting [wasm-shim](https://github.com/Kuadrant/wasm-shim) module compliant with the Envoy's [Rate Limit Service (RLS)](https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/ratelimit/v3/rls.proto). This wasm-shim module accepts a [PluginConfig](https://github.com/Kuadrant/kuadrant-operator/blob/fa2b52967409b7c4ea2c2e3412ecf80a8ad2b802/pkg/istio/wasm.go#L24) struct object as input configuration object.
+On designing Kuadrant's rate limiting and considering Istio/Envoy's rate limiting offering, we hit two limitations ([described here](https://docs.google.com/document/d/1ve_8ZBq8TK_wnAZHg69M6-f_q1w-mX4vuP1BC1EuEO8/edit#bookmark=id.5wyq2fj56u94)). Therefore, not giving up entirely in existing [Envoy's RateLimit Filter](https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/filters/network/ratelimit/v3/rate_limit.proto#extension-envoy-filters-network-ratelimit), we decided to move on and leverage the Envoy's [Wasm Network Filter](https://www.envoyproxy.io/docs/envoy/latest/configuration/listeners/network_filters/wasm_filter) and implement rate limiting [wasm-shim](https://github.com/Kuadrant/wasm-shim) module compliant with the Envoy's [Rate Limit Service (RLS)](https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/ratelimit/v3/rls.proto). This wasm-shim module accepts a [PluginConfig](https://github.com/Kuadrant/kuadrant-operator/blob/fa2b52967409b7c4ea2c2e3412ecf80a8ad2b802/pkg/istio/wasm.go#L24) struct object as input configuration object.
## Use Cases targeting a gateway
A key use case is being able to provide governance over what service providers can and cannot do when exposing a service via a shared ingress gateway. As well as providing certainty that no service is exposed without my ability as a cluster administrator to protect my infrastructure from unplanned load from badly behaving clients etc.
@@ -24,7 +24,7 @@ The goal of this document is to define:
* The kuadrant-operator behavior filling the `PluginConfig` struct having as input the RateLimitPolicy k8s objects
* The behavior of the wasm-shim having the `PluginConfig` struct as input.
-## Envoy's Rate Limit Service Potocol
+## Envoy's Rate Limit Service Protocol
Kuadrant's rate limit relies on the [Rate Limit Service (RLS)](https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/ratelimit/v3/rls.proto)
protocol, hence the gateway generates, based on a set of
diff --git a/doc/ratelimitpolicy-reference.md b/doc/ratelimitpolicy-reference.md
index 61bd77092..cb1fab1c7 100644
--- a/doc/ratelimitpolicy-reference.md
+++ b/doc/ratelimitpolicy-reference.md
@@ -18,64 +18,64 @@ Generated using [github-markdown-toc](https://github.com/ekalinin/github-markdow
## RateLimitPolicy
-| **json/yaml field**| **Type** | **Required** | **Description** |
-| --- | --- | --- | --- |
-| `spec` | [RateLimitPolicySpec](#RateLimitPolicySpec) | Yes | The specfication for RateLimitPolicy custom resource |
-| `status` | [RateLimitPolicyStatus](#RateLimitPolicyStatus) | No | The status for the custom resource |
+| **json/yaml field** | **Type** | **Required** | **Description** |
+|---------------------|-------------------------------------------------|--------------|------------------------------------------------------|
+| `spec` | [RateLimitPolicySpec](#RateLimitPolicySpec) | Yes | The specfication for RateLimitPolicy custom resource |
+| `status` | [RateLimitPolicyStatus](#RateLimitPolicyStatus) | No | The status for the custom resource |
## RateLimitPolicySpec
-| **json/yaml field**| **Type** | **Required** | **Default value** | **Description** |
-| --- | --- | --- | --- | --- |
-| `targetRef` | [gatewayapiv1alpha2.PolicyTargetReference](https://github.com/kubernetes-sigs/gateway-api/blob/main/apis/v1alpha2/policy_types.go) | Yes | N/A | identifies an API object to apply policy to |
-| `rateLimits` | [][RateLimit](#RateLimit) | No | empy list | list of rate limit configurations |
+| **json/yaml field** | **Type** | **Required** | **Default value** | **Description** |
+|---------------------|------------------------------------------------------------------------------------------------------------------------------------|--------------|-------------------|---------------------------------------------|
+| `targetRef` | [gatewayapiv1alpha2.PolicyTargetReference](https://github.com/kubernetes-sigs/gateway-api/blob/main/apis/v1alpha2/policy_types.go) | Yes | N/A | identifies an API object to apply policy to |
+| `rateLimits` | [][RateLimit](#RateLimit) | No | empy list | list of rate limit configurations |
### RateLimit
-| **json/yaml field**| **Type** | **Required** | **Default value** | **Description** |
-| --- | --- | --- | --- | --- |
-| `configurations` | [][Configuration](#Configuration) | No | Empty | list of action configurations |
-| `rules` | [][Rule](#Rule) | No | Empty. All configurations apply | list of action configurations rules. Rate limit configuration will apply when at least one rule matches the request |
-| `limits` | [][Limit](#Limit) | No | Empty | list of Limitador limit objects |
+| **json/yaml field** | **Type** | **Required** | **Default value** | **Description** |
+|---------------------|-----------------------------------|--------------|---------------------------------|---------------------------------------------------------------------------------------------------------------------|
+| `configurations` | [][Configuration](#Configuration) | No | Empty | list of action configurations |
+| `rules` | [][Rule](#Rule) | No | Empty. All configurations apply | list of action configurations rules. Rate limit configuration will apply when at least one rule matches the request |
+| `limits` | [][Limit](#Limit) | No | Empty | list of Limitador limit objects |
#### Configuration
-| **json/yaml field**| **Type** | **Required** | **Default value** | **Description** |
-| --- | --- | --- | --- | --- |
-| `actions` | [][ActionSpecifier](#ActionSpecifier) | No | empty | list of action specifiers. Each action specifier can only define one action type. |
+| **json/yaml field** | **Type** | **Required** | **Default value** | **Description** |
+|---------------------|---------------------------------------|--------------|-------------------|-----------------------------------------------------------------------------------|
+| `actions` | [][ActionSpecifier](#ActionSpecifier) | No | empty | list of action specifiers. Each action specifier can only define one action type. |
#### ActionSpecifier
-| **json/yaml field**| **Type** | **Required** | **Default value** | **Description** |
-| --- | --- | --- | --- | --- |
-| `generic_key` | [config.route.v3.RateLimit.Action.GenericKey](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-generickey) | No | null | generic key action |
-| `metadata` | [config.route.v3.RateLimit.Action.MetaData](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-metadata) | No | null | descriptor entry is appended when the metadata contains a key value |
-| `remote_address` | [config.route.v3.RateLimit.Action.RemoteAddress](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-remoteaddress) | No | null | descriptor entry is appended to the descriptor and is populated using the trusted address from x-forwarded-for |
-| `request_headers` | [config.route.v3.RateLimit.Action.RequestHeaders](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-requestheaders) | No | null | descriptor entry is appended when a header contains a key that matches the header_name |
+| **json/yaml field** | **Type** | **Required** | **Default value** | **Description** |
+|---------------------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|--------------|-------------------|----------------------------------------------------------------------------------------------------------------|
+| `generic_key` | [config.route.v3.RateLimit.Action.GenericKey](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-generickey) | No | null | generic key action |
+| `metadata` | [config.route.v3.RateLimit.Action.MetaData](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-metadata) | No | null | descriptor entry is appended when the metadata contains a key value |
+| `remote_address` | [config.route.v3.RateLimit.Action.RemoteAddress](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-remoteaddress) | No | null | descriptor entry is appended to the descriptor and is populated using the trusted address from x-forwarded-for |
+| `request_headers` | [config.route.v3.RateLimit.Action.RequestHeaders](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-ratelimit-action-requestheaders) | No | null | descriptor entry is appended when a header contains a key that matches the header_name |
#### Rule
-| **json/yaml field**| **Type** | **Required** | **Default value** | **Description** |
-| --- | --- | --- | --- | --- |
-| `paths` | []string | No | null | list of paths. Request matches when one from the list matches |
-| `methods` | []string | No | null | list of methods to match. Request matches when one from the list matches |
-| `hosts` | []string | No | null | list of hostnames to match. Wildcard hostnames are valid. Request matches when one from the list matches. Each defined hostname must be subset of one of the hostnames defined by the targeted network resource |
+| **json/yaml field** | **Type** | **Required** | **Default value** | **Description** |
+|---------------------|----------|--------------|-------------------|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
+| `paths` | []string | No | null | list of paths. Request matches when one from the list matches |
+| `methods` | []string | No | null | list of methods to match. Request matches when one from the list matches |
+| `hosts` | []string | No | null | list of hostnames to match. Wildcard hostnames are valid. Request matches when one from the list matches. Each defined hostname must be subset of one of the hostnames defined by the targeted network resource |
#### Limit
-| **json/yaml field**| **Type** | **Required** | **Default value** | **Description** |
-| --- | --- | --- | --- | --- |
-| `maxValue` | int | Yes | N/A | max number of request for the specified time period |
-| `seconds` | int | Yes | N/A | time period in seconds |
-| `conditions` | []string | No | Empty list | Limit conditions. Check [Limitador](https://github.com/Kuadrant/limitador) for more information |
-| `variables` | []string | No | Empty list | Limit variables. Check [Limitador](https://github.com/Kuadrant/limitador) for more information |
+| **json/yaml field** | **Type** | **Required** | **Default value** | **Description** |
+|---------------------|----------|--------------|-------------------|-------------------------------------------------------------------------------------------------|
+| `maxValue` | int | Yes | N/A | max number of request for the specified time period |
+| `seconds` | int | Yes | N/A | time period in seconds |
+| `conditions` | []string | No | Empty list | Limit conditions. Check [Limitador](https://github.com/Kuadrant/limitador) for more information |
+| `variables` | []string | No | Empty list | Limit variables. Check [Limitador](https://github.com/Kuadrant/limitador) for more information |
## RateLimitPolicyStatus
-| **json field **| **Type** | **Info** |
-| --- | --- | --- |
-| `observedGeneration` | string | helper field to see if status info is up to date with latest resource spec |
-| `conditions` | array of [condition](#ConditionSpec)s | resource conditions |
+| **json field** | **Type** | **Info** |
+|----------------------|---------------------------------------|----------------------------------------------------------------------------|
+| `observedGeneration` | string | helper field to see if status info is up to date with latest resource spec |
+| `conditions` | array of [condition](#ConditionSpec)s | resource conditions |
### ConditionSpec
@@ -89,10 +89,10 @@ Each element of the Condition array has the following fields:
* The *type* field is a string with the following possible values:
* Available: the resource has successfully configured;
-| **Field** | **json field**| **Type** | **Info** |
-| --- | --- | --- | --- |
-| Type | `type` | string | Condition Type |
-| Status | `status` | string | Status: True, False, Unknown |
-| Reason | `reason` | string | Condition state reason |
-| Message | `message` | string | Condition state description |
-| LastTransitionTime | `lastTransitionTime` | timestamp | Last transition timestamp |
+| **Field** | **json field** | **Type** | **Info** |
+|--------------------|----------------------|-----------|------------------------------|
+| Type | `type` | string | Condition Type |
+| Status | `status` | string | Status: True, False, Unknown |
+| Reason | `reason` | string | Condition state reason |
+| Message | `message` | string | Condition state description |
+| LastTransitionTime | `lastTransitionTime` | timestamp | Last transition timestamp |
diff --git a/doc/user-guides/authenticated-rl-for-api-owners.md b/doc/user-guides/authenticated-rl-for-api-owners.md
index f2751c313..124966a85 100644
--- a/doc/user-guides/authenticated-rl-for-api-owners.md
+++ b/doc/user-guides/authenticated-rl-for-api-owners.md
@@ -1,4 +1,4 @@
-## Authenticated Rate Limit For API Owners
+# Authenticated Rate Limit For API Owners
This user guide shows how to configure authenticated rate limiting.
Authenticated rate limiting allows to specify rate limiting configurations
@@ -7,8 +7,8 @@ Authentication method used will be the API key.
### Clone the project
-```
-git clone https://github.com/Kuadrant/kuadrant-operator
+```sh
+git clone https://github.com/Kuadrant/kuadrant-operator && cd kuadrant-operator
```
### Setup environment
@@ -22,7 +22,7 @@ make local-setup
### Apply Kuadrant CR
-```yaml
+```sh
kubectl -n kuadrant-system apply -f - <
- 🤔 What exactly does the step above do?
-
- 1. Creates a containerized Kuberentes server using [Kind](https://kind.sigs.k8s.io/)
- 2. Installs [Istio](https://istio.io)
- 3. Installs Kuberentes [Gateway API](https://gateway-api.sigs.k8s.io/concepts/api-overview)
- 4. Installs the Kuadrant system (CRDs and operators)
-
-
-### ❷ Deploy the API
+### ❸ Deploy the API
Deploy the application in the `default` namespace:
@@ -49,12 +41,6 @@ Create the `HTTPRoute`:
kubectl apply -f examples/toystore/httproute.yaml
```
-Expose the API:
-
-```sh
-kubectl port-forward -n istio-system service/istio-ingressgateway 9080:80 2>&1 >/dev/null &
-```
-
#### API lifecycle
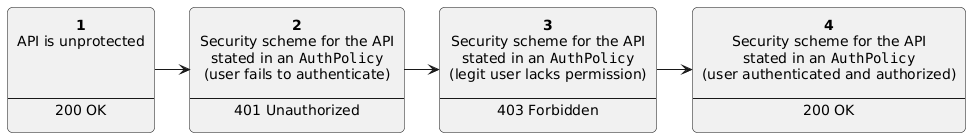
@@ -66,19 +52,29 @@ curl -H 'Host: api.toystore.com' http://localhost:9080/toy -i
# HTTP/1.1 200 OK
```
-### ❸ Request the Kuadrant instance
+It should return `200 OK`.
+
+**Note**: This only works out of the box on linux environments. If not on linux,
+you may need to forward ports
+
+```bash
+kubectl port-forward -n istio-system service/istio-ingressgateway 9080:80 &
+```
+
+### ❹ Request the Kuadrant instance
```sh
-kubectl apply -f -<
- 🤔 Can I use Roles and RoleBindings instead of ClusterRoles and ClusterRoleBindings?
+ Can I use Roles and RoleBindings instead of ClusterRoles and ClusterRoleBindings?
Yes, you can.
@@ -279,10 +279,10 @@ curl -H "Authorization: Bearer $SA_TOKEN" -H 'Host: api.toystore.com' -X POST ht
# HTTP/1.1 403 Forbidden
```
-### ❼ Create the `RateLimitPolicy`
+### ❽ Create the `RateLimitPolicy`
```sh
-kubectl apply -f -< **Note:** It may take a couple minutes for the RateLimitPolicy to be applied depending on your cluster.
+> **Note:** It may take a couple of minutes for the RateLimitPolicy to be applied depending on your cluster.
#### Try the API rate limited
diff --git a/doc/user-guides/gateway-rl-for-cluster-operators.md b/doc/user-guides/gateway-rl-for-cluster-operators.md
index 22212128b..af5bb56c1 100644
--- a/doc/user-guides/gateway-rl-for-cluster-operators.md
+++ b/doc/user-guides/gateway-rl-for-cluster-operators.md
@@ -1,4 +1,4 @@
-## Gateway Rate Limit For Cluster Operators
+# Gateway Rate Limit For Cluster Operators
This user guide shows how the kuadrant's control plane applies rate limit policy at
[Gateway API's Gateway](https://gateway-api.sigs.k8s.io/v1alpha2/references/spec/#gateway.networking.k8s.io/v1beta1.Gateway)
@@ -6,8 +6,8 @@ level.
### Clone the project
-```
-git clone https://github.com/Kuadrant/kuadrant-operator
+```sh
+git clone https://github.com/Kuadrant/kuadrant-operator && cd kuadrant-operator
```
### Setup environment
@@ -15,13 +15,13 @@ git clone https://github.com/Kuadrant/kuadrant-operator
This step creates a containerized Kubernetes server locally using [Kind](https://kind.sigs.k8s.io),
then it installs Istio, Kubernetes Gateway API and kuadrant.
-```
+```sh
make local-setup
```
### Apply Kuadrant CR
-```yaml
+```sh
kubectl -n kuadrant-system apply -f - <